I accidentally got my 4th CVE.
CVE ID: CVE-2021-44148
Don’t get too excited, it’s just an XSS. Just a standard XSS.
I’m about to go full recipe blog:
The story of this CVE begins in 2014 when I first heard of the wifi pineapple from Hak5. At the time, I was working in IT making 30k a year and paying for my ex-wife to go to college. I did not have $100 bucks or whatever it was to drop on a wifi-pineapple. In 2016 I saw blog articles like these:
http://sapinski.com/2016/02/13/wifi-pineapple-firmware-for-gl-inet-gl-ar150/
https://www.securityaddicted.com/2016/11/17/weaponizing-gl-inet-gl-ar150/
All claiming you could buy a $25 mini router and turn it into a wifi pineapple. I instantly bought one.
But because of my 2x diagnosed ADHD/ADD I never even got as far as installing the wifi pineapple firmware. It had taken about a week to get to my house and by that time I had become obsessed with something else.
Fast forward to 2019.
I started working as a pentester in July-ish of 2019. Specifically working on web application pentests. At this time whenever I see something on Twitter or LinkedIn about something web-app pentest or bug bounty related, I read it. I came across this blog post:
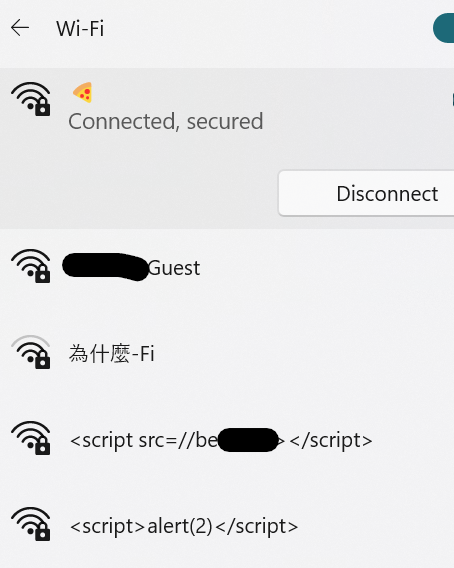
Reading this made me realize that literally any input could be an XSS and I thought to myself I may as well make an XSS SSID just in case for the future. I have Ubiquiti equipment at home so it was easy enough to create an SSID called <script>alert(2)<script>. Keep in mind that SSID’s have to be less than 32 characters.
Fast forward again to late 2021.
The pandemic has been “almost over” for a year now.
People are starting to go back into the office. I can’t really talk about what I was working on but for a pentest I needed a little router. I remembered back when I bought my GL-AR150 in 2016. I had since moved 5 times. In my last move I decided to index everything that was in each box so I found it relatively fast.
I plugged it in and connected to the default network it provided. After setting a root password, I logged in and started navigating around the menus to see if anything would be helpful for my pentest or if I should just install default openwrt.
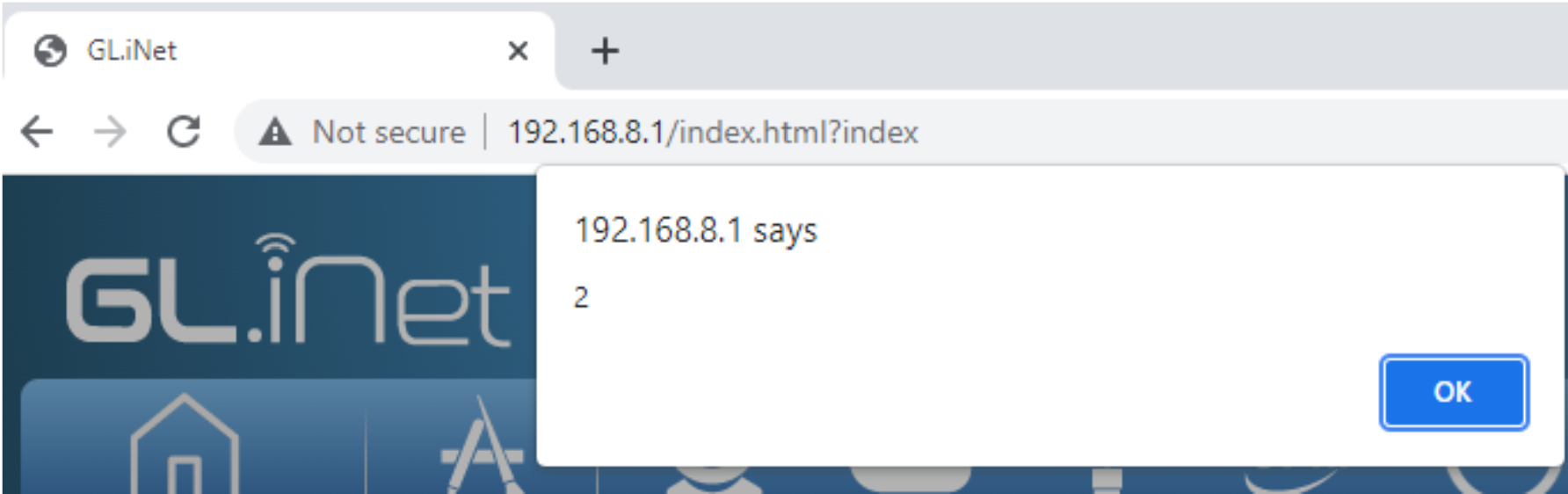
Seemingly out of nowhere I get this popup. For about 4 seconds I was like “WUT….” and then it all clicked. I was on the repeater page where it searches for wifi networks. My SSID that I had made in 2019 finally did something.
At this point I just started laughing. I couldn’t believe it. My wife thought something was wrong because of the noises that were coming out of my home office.
I didn’t have time to create a real XSS payload like I normally do but I still felt good about finding this one. I decided to take it just one step further using xsshunter.com.
As you remember an SSID can only be 32 characters. So my normal xsshunter payloads weren’t going to work. So instead I followed this blog post and created a short domain that forwarded to my normal xsshunter payload page:
So now I have an SSID that has my xsshunter payload in it just in case this happens again. So now I’ll get notifications:

Something else to remember is that this was purchased in 2016. It had an extremely old firmware on it. So when I found this bug it was running on firmware version 2.19 and the bug was fixed in version 3 of the firmware. The current version as of writing is 3.203. More can be found here:
https://docs.gl-inet.com/en/3/release_notes/
TL;DR
XSS payload as WiFi SSID leads to reflected XSS.
Timeline:
- Nov 16th 2021 Found bug
- Nov 17th 2021 Notified company of bug via email
- Bug has already been fixed in version 3.x of firmware.
- Nov 20th submit for CVE
- Nov 22nd CVE reserved
